The FBI’s Internet Crime Complaint Center (IC3)recently published their 2017 Internet Crime Report. The report contains statistics on the state of crimes reported to the FBI throughout the year. The stats are not a comprehensive roll-up of all crime as many incidents still don’t get reported to the FBI. They do, however, provide a glimpse into what issues are affecting us Internet denizens. Also included are some solutions that may help lessen the likelihood and impact of you falling victim to some of the more common crimes.
Annual Statistics
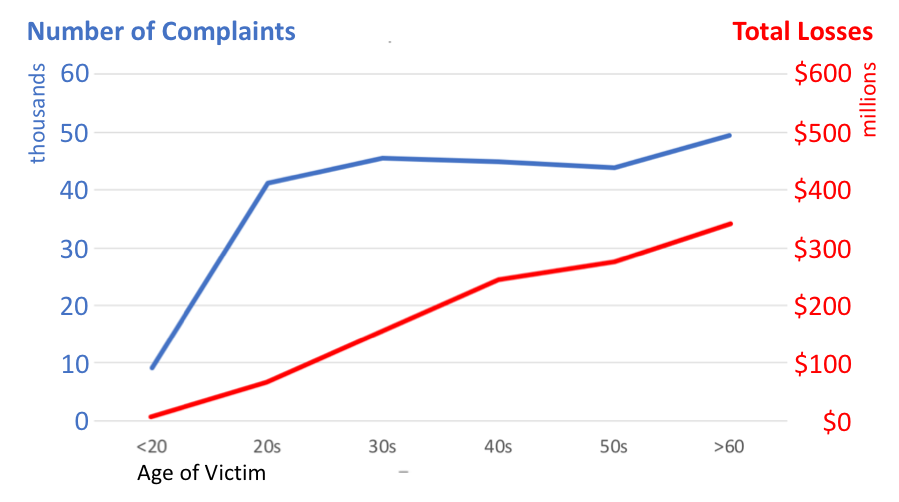
The report provides a breakdown of the victims by age. It is of note that the volume of incidents is relatively consistent across all the adult age brackets, but the burden of the losses is proportionally shouldered by the older age brackets. This shows that criminals target everyone equally but have the most gains when targeting older victims.
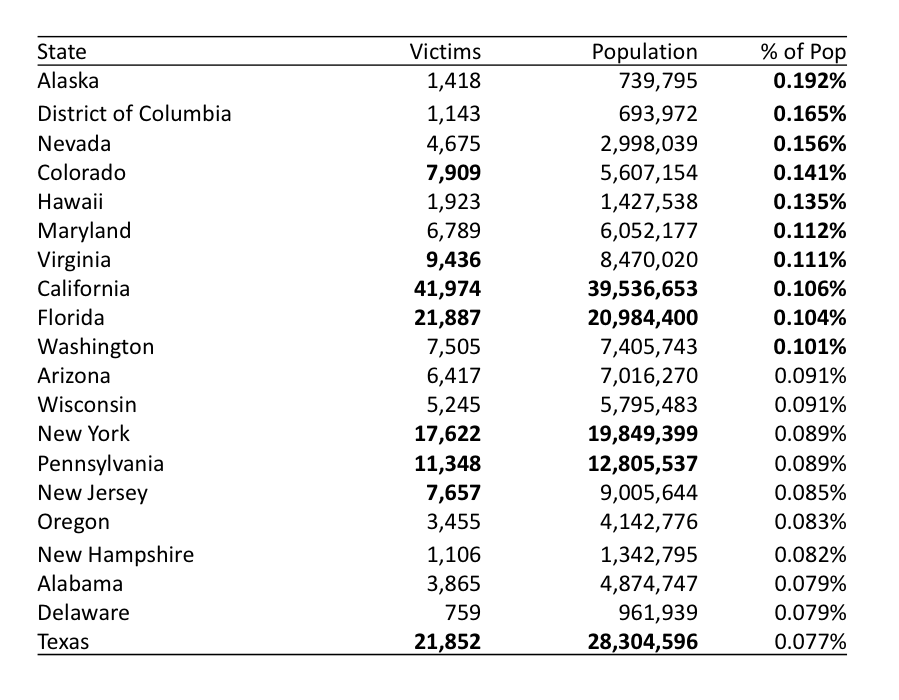
The report presents a top ten list of the states which had the most victims and most total losses. I found listing the states by the raw numbers without tempering the data to be interesting, but it doesn’t tell the whole story. California topped the report’s list with twice the number of victims as the states in the second and third position on the list combined, but that shouldn’t be a surprise since California’s population is significantly higher than the two next most populated states – more people in general means more victims.
To normalize the data, I ranked the states by the percentage of victims to total state population in the most recent estimates. This is the population equivalent of “adjusted for inflation”. The numbers in bold are the top ten highest values from each column. By sorting by the percentage, a very different top ten list emerges from the one presented in the report, one which includes only four of the report’s top ten. These seem to be the states that are attacked more per capita.
The report also provides two lists of the top crimes by type ranked by the number of victims reported and by the total losses reported. As with the by state breakdown, I felt that listing the raw numbers alone did not properly weight the crimes by the impact they have on their victims. To attempt to understand the impact, I provide below a list that is ranked by the average loss per victim, in an attempt to show which crimes have the potential for greater fiscal impact. The numbers in bold are the top ten highest values from each column.
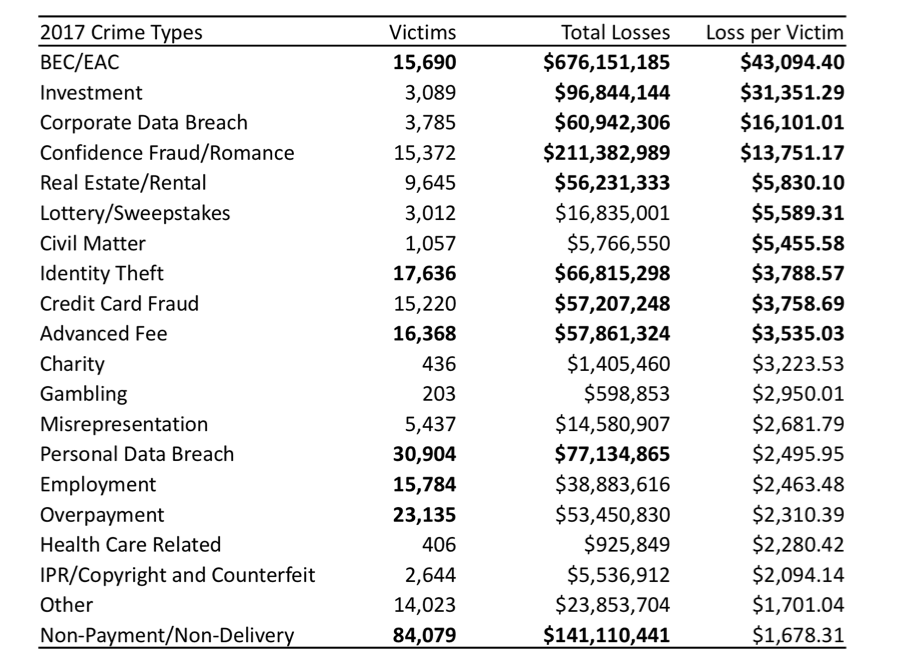
From this we can see that Business Email Compromise, which made the top of the report’s list by total losses, is clearly the most damaging crime felt by the victims. Investment fraud is the second-most likely to take victims for larger amounts of money, even though the frequency of occurrence appears to be very low by comparison to other crimes. On the opposite end of the scale, we can see that Non-payment/Non-delivery fraud targeting retailers and their customers has a low per-incident impact, but its very high rate of occurrence causes it to appear at the top of the list of ranking by victim count and third on the ranking by total losses.
Two of the top loss leaders are cybercrimes that occur nearly daily that we all need to be wary of, Business Email Compromise and Data Breaches. Let’s take a look at what we can do to protect ourselves from these attacks.
Business Email Compromise
The category of crime that nets the most money for criminals is Business Email Compromise or Email Account Compromise (BEC/EAC). The IC3 reports 15,690 BEC/EAC incidents with total losses of over $676 million. BEC is a common scam that involves criminals sending targeted phishing emails to employees pretending to either be senior management of the company or a customer and requesting that funds be transferred to a specified account. The EAC variant of this scam involves criminals taking control of an employee’s email account in order to send the emails as that person rather than attempting to spoof an email. Most often the funds are then transferred via wire transfer or some other electronic funds transfer, but sometimes also a check might be written. These losses can be in the millions and are often very difficult to recoup the funds.
Solutions
Here are some common security controls that can help mitigate against these scams.
SECURITY AWARENESS TRAINING – First, regular security awareness training for your employees is vital. They should be aware of these scams so they can recognize them as they are happening. They should know how to recognize spam and phishing emails, to not click on the links, and how to properly report them. In addition to BEC, spam and phishing are the most common ways for attackers to deliver malware in order to break into your network, so this knowledge will really help protect the enterprise from attacks.
DUAL AUTHORIZATION – Another important control is dual authorization, where two people are required to initiate a funds transfer. This way there is a second set of eyes on every transfer to catch any irregularities. Separation of duties so that one person enters the transaction and then a different person authorizes and transmits the transaction help to prevent fraud, catch data entry errors, and catch other similar issues before they become issues.
OUT-OF-BAND VERIFICATION – Most importantly, out-of-band verification on suspicious transfers, especially when they are requested via email. Practically every BEC funds loss could have been avoided with a phone call to verify the validity of transfer request. Understanding that transactions volumes are usually such that requiring a manual authorization on every transfer is most certainly a burden, but the likelihood and frequency of fraud via BEC more than justifies requiring a verification on any requests that come via email or that seem out of the normal course of business.
Data Breaches
Losses attributed to Identity Theft, Credit Card Fraud, and both Corporate and Personal Data Breaches reached a combined total loss of over $262 million in 2017. The report itemizes these categories out, but they are all related to criminals stealing and misusing personally identifiable information (PII). This includes crimes such as theft of credit card information stored by a retailer, theft and misuse of banking credentials, and even opening new lines of credit in the victim’s name.
Most of these data breaches start with malware that is installed via spam or a compromised website. Victims of these attacks are equally targeted both at work and at home, though corporate enterprises typically invest more in security than home networks resulting in a high success rate among home users. Credit card fraud accounts for almost half of these losses, but this is the half that is easiest for consumers to recover from. Fraudulent charges on a credit card are typically reversed by the card brands and the losses are shouldered by either the card brand or the originating merchant.
The more damaging attacks for consumers are the various forms of fraud that make up the other half of these losses, which includes filing fraudulent tax returns, opening new lines of credit, or initiating fraudulent debit or ACH transactions. It is considerably harder for the consumer to recuperate the lost funds in these types of fraud, and sometimes the damaging effects can linger on credit reports for many years.
Solutions
Here are a few things consumers can do to protect themselves and employees should do protect their companies from these scams.
SPAM AWARENESS – Spam is ever present on the Internet at volumes that are unimaginable. Most corporate environments and most consumer email providers offer some level of spam filtering, but some percentage will always sneak through to your inbox. Security Awareness training to sensitize users on how to identify and handle spam is a vital first line of defense to these attacks.
CREDIT MONITORING – There are numerous credit monitoring services that will assist in notifying consumers of changes to their credit reports. This can help identify if a scammer is trying to open a mortgage, loan, credit card, or other line of credit in your name. The sooner you identify the problem, the easier it is to stop it and the less financial impact it will have.
CREDIT FREEZE – A more preventative solution is a credit freeze. For a fee, consumers can lock their credit reports. This will effectively prevent any new lines of credit from being opened in your name. This must be done multiple times, once for each of the three major credit bureaus. It will also prevent you from opening legitimate credit inquiries, so you have to unfreeze your reports if you ever want to apply for a new credit card, loan, or similar account, and then freeze the reports again afterwards. This incurs fees every time the report is frozen or unfrozen and can be a burden, but it does effectively protect you from identity theft fraud related to scammers opening new accounts in your name. Brian Krebshas coveredthismultipletimes.
TWO-FACTOR AUTHENTICATION – Much of this fraud is based on account credential theft, or put more plainly, bad guys stealing your password and logging into your accounts. Activating two-factor authentication, where in addition to your password you have to also supply a second temporary password that is provided via email, text message, or some token or app, will help keep bad guys out of your accounts since they cannot use the password they stole unless they are also able to somehow also intercept your text messages, emails, or enroll a new token. Important accounts to apps that contain sensitive data, such as logging into your bank web site or VPN access to an enterprise network, should require two-factor authentication.
Confidence Fraud
The third most costly category of crimes are Confidence or Romance Fraud, with reported total losses of over $211 million in 2017. This is when a scammer tricks a victim into believing they have a trust relationship and then persuades the victim to send money, reveal financial information, or launder money on behalf of the scammer.
A common form of this attack is called the Grandparent’s Scam. In this crime, the scammer contacts an elderly victim pretending to be a grandchild in need. A common angle is for the scammer to pretend they are in some sort of personal emergencyand in need money, for instance due to a family illness, a mugging, or some other unfortunate event, or to claim they want to come visit but need money to cover travel. There are also related scams that exploit health care needs, contest winnings, or supporting fake charities.
The increase in online dating as seen the inevitable increase in online dating scams. This frequently manifests itself as fake accounts controlled by automated programs, called bots, which send tempting photos and flirtations in order to lure in potential victims. Once engaged, the bot will direct the victim to a link that installs malware, steals financial information, or other attempts to illicit financial gains from the victim.
Solutions
Here are a few things consumers can do to protect themselves can do protect themselves from these scams.
AWARENESS – Recognizing these scams greatly increases a person’s chances of not becoming a victim. Security Awareness training into various online scams will raise awareness and lessen the likelihood of falling for the temptations presented by these scammers.
VERIFY IDENTITIES – When anyone contacting you online begins requesting money or other sensitive information, always verify the identity of the person and the veracity of the claims. Many of these scams require convincing the victim that they scammer is a relative or other person of trust. If someone contacts you purporting to be someone you know from a source you don’t normally talk to them via, such as a new phone number or a different social media account, contact them or a mutual connection to verify the number, account, or address actually belongs to the person they claim to be.
A BIT OF PARANOIA – Being skeptical of requests for money or personal information can be a very good thing. If anything doesn’t feel right, it probably isn’t. If the person’s grammar doesn’t match their purported background, the pictures in the profile don’t seem to match the person talking, or the situation just seems too good to be true, you are quite likely dealing with a scammer.
Stay Safe Out There
Crime on the Internet is not going away any time soon, but you can protect yourself and your enterprise networks. These security practices won’t make the threats go away but will make it harder for the criminals and hopefully be enough to persuade them to find an easier target.
